We're updating our Terms of Service to ensure fairness and sustainability of our Free Plan: learn what's changing and how it affects you.
What is X.509 TLS client-certificate authentication?
Client-Certificate Authentication is a mutual certificate based authentication, where users provide digital certificates compliant with the X.509 standards to the Verifalia servers to prove their identities, as part of the TLS protocol handshake; this is also called mutual or two-way TLS authentication. In fact, while TLS’s primary function on the Internet is to facilitate encryption and trust that allows a web browser to validate the authenticity of a web site, the protocol works the other way around too, with X.509 client certificates used to authenticate a client to the web server.
Using client-certificate authentication
Authenticating to Verifalia using a client certificate requires the user to have that authentication method enabled on the Authentication tab, as shown in the following screenshot:
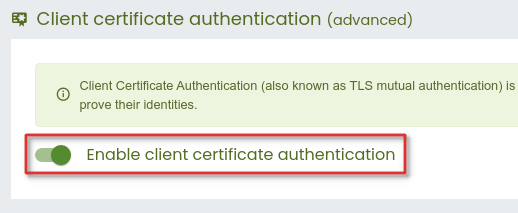
Each X.509 client certificate must also be bound to the requesting Verifalia user through the Client certificates interface (available by way of the Manage client certificates (X.509)... link on the Authentication tab): while it is possible to use client certificates signed by a public certificate authority, organizations often set up a private certificate authority to issue client certificates. Certificates signed by a public certificate authority are expensive and are generally unnecessary, as Verifalia uses client certificates just as a transport for the public key, whose authenticity is established by an out-of-band mechanims (PKI-less CCA). See also: how to create a self-signed X.509 client certificate for TLS mutual authentication?
Client certificates can be uploaded, managed and removed by way of the aforementioned Client certificates interface. While handling a client certificate file upload, we support base64-encoded format (usually found with the file extensions .pem, .crt and .cer) or binary format (DER, usually found with the file extensions .der and .cer). Also, for additional security and compliancy with the RFC 5280, we accept only X.509 client certificates including the extended key usage extension id-kp-clientAuth (OID 1.3.6.1.5.5.7.3.2).
Here is how the Client certificates interface looks like, with a client certificate bound:
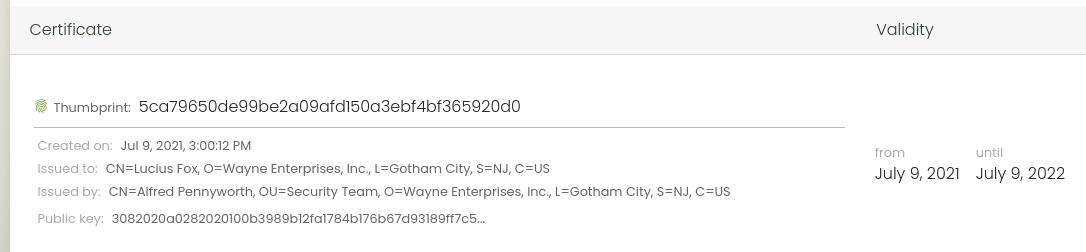
Client-certificate authentication is currently available for our API consumers only (and not through our web-based dashboard); also we currently accept a maximum of 5 client certificates per each Verifalia user.
API endpoints
Verifalia provides dedicated API endpoints for users authenticating using an X.509 client certificate: please see our API reference guide for additional details and sample usage.