We're updating our Terms of Service to ensure fairness and sustainability of our Free Plan: learn what's changing and how it affects you.
What are trusted origins and how can I configure them?
When you enable the trusted origins feature, you restrict the usage of your browser app to a predefined list of trusted websites, adding an essential layer of security to your application. In the context of web development, the term origin refers to the combination of the domain and protocol (e.g., https://www.example.com) from which a request is made: while it's theoretically possible for malicious users to attempt to spoof their origin, modern web browsers are designed to always send the correct origin value according to IETF specifications (see RFC 6454 for the technical details).
By leveraging this predictable behavior, trusted origins helps prevent unauthorized usage of your web application, ensuring that only requests from approved sources are processed: any request originating from a domain not in this list will be automatically blocked. Of course, this functionality is particularly valuable when you are using our embeddable email verification widget, as it ensures that the widget cannot be misused by third parties on unauthorized sites.
Defining trusted origins
The trusted origins feature supports the use of wildcard expressions, giving you flexibility in specifying which websites are permitted to use your application. Wildcard expressions are patterns that allow you to define groups of domains and protocols without explicitly listing each one:
- the
*wildcard matches any number of characters, including none; - the
?wildcard matches exactly one character.
Below are some examples of how you can use wildcard expressions to configure trusted origins:
Specific website
https://www.example.com - No wildcards: this allows access only from the specific site https://www.example.com.
All subdomains
https://*.example.com - This permits access from any subdomain of example.com, such as https://www.example.com or https://foo.example.com, as long as the request uses the HTTPS protocol. Note that this expression does not include the specific website https://example.com
Multiple protocols
http*://example.com - This allows access to example.com using either HTTP or HTTPS protocols, ensuring flexibility in development and deployment scenarios.
These options empower you to configure security settings that align with the specific needs of your application.
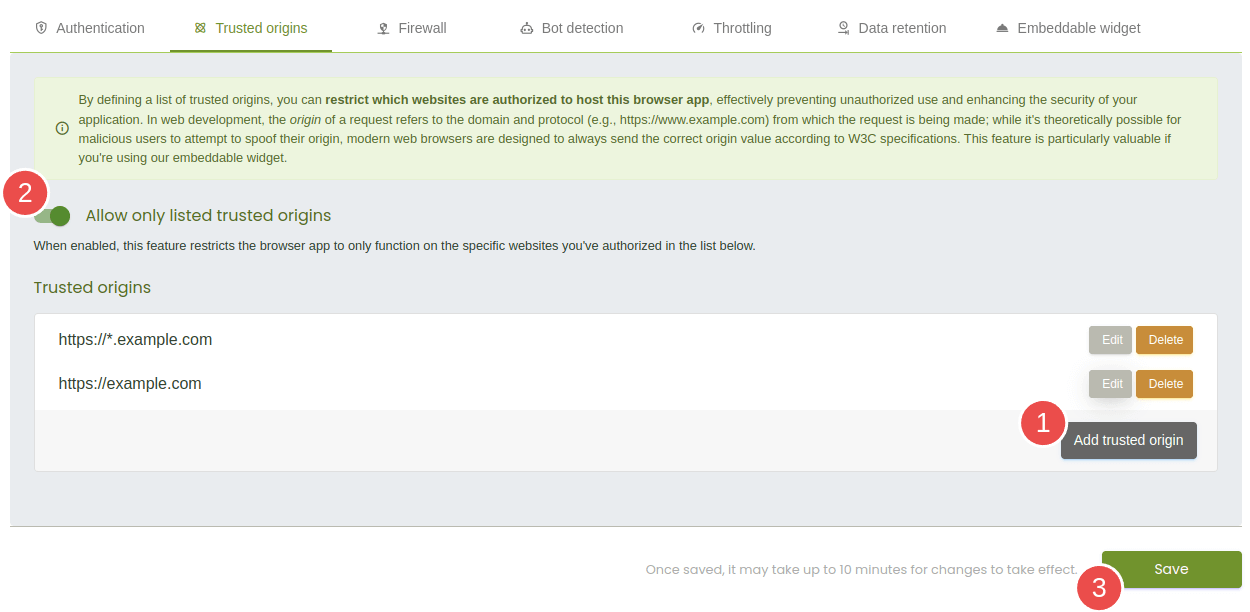
Setting up trusted origins
To implement trusted origins, navigate to the settings for your browser app in the Verifalia client area and follow these steps:
- Click the Add trusted origin button to define one or more wildcard expressions based on your requirements. This creates a list of trusted origins authorized to host your browser app.
- Toggle the Allow only listed trusted origins setting to activate the feature. This restricts the browser app to operate only on the domains specified in your list.
- After configuring your trusted origins, click the Save button to apply the changes.